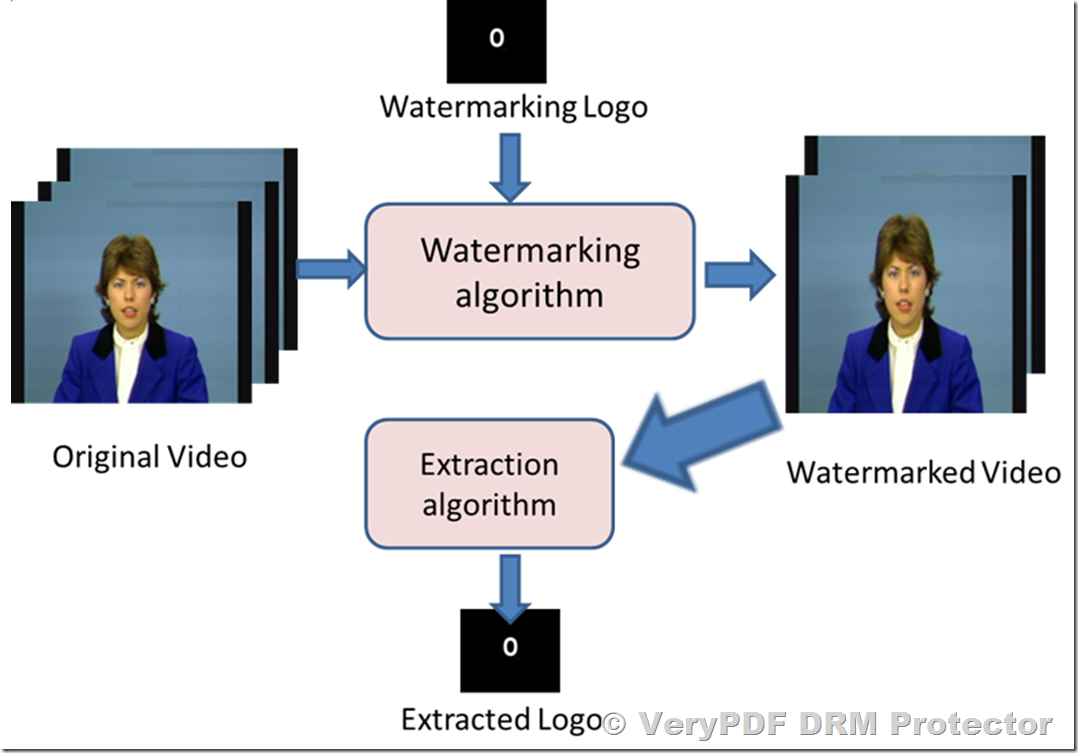
In the rapidly evolving landscape of digital intellectual property, the battle between content creators and unauthorized redistributors is constant. As traditional security measures like password protection and standard encryption are increasingly circumvented by sophisticated “analog hole” attacks, such as screen capturing and high-resolution photography, a more resilient solution is required.
VeryPDF DRM Protector is meeting this challenge head-on by integrating Blind Watermarking (Invisible Digital Watermarking) technology. This article explores how this forensic-level security layer works, why it is superior to traditional methods, and how it empowers organizations to protect their most sensitive PDF assets.
1. Understanding the Concept: Blind Watermarking vs. Visible Watermarking
To appreciate the value of Blind Watermarking, one must first understand the limitations of visible markers. For decades, the “Visible Watermark” (the translucent text or logo overlaying a page) has been the go-to for copyright notice. However, visible watermarks suffer from two fatal flaws:
-
Aesthetic Disruption: They interfere with the readability of technical diagrams, medical reports, and premium e-books.
-
Easy Removal: Sophisticated AI-driven image editing tools can now “fill in” the pixels behind a visible watermark, effectively erasing it.
Blind Watermarking by VeryPDF operates on a different plane. It is a form of steganography where information is hidden within the digital noise or the mathematical representation of the document’s content. To the human eye, the document looks identical to the original. To a computer algorithm, however, the document contains a wealth of hidden metadata—be it a transaction ID, a user email, or a timestamp.
2. The Technical Core: How VeryPDF Implements Blind Watermarking
VeryPDF DRM Protector does not simply hide text in a hidden PDF layer. Instead, it utilizes Transform Domain Watermarking, a sophisticated digital signal processing technique.
A. Frequency Domain Embedding
Most basic watermarks operate in the “spatial domain” (changing pixel values directly). These are easily destroyed by resizing. VeryPDF utilizes the Frequency Domain, employing algorithms like:
-
Discrete Cosine Transform (DCT): Similar to how JPEG compression works, we embed data in the middle-frequency bands. This ensures the watermark is robust enough to survive compression but subtle enough not to create visual artifacts.
-
Discrete Wavelet Transform (DWT): This allows for “multi-resolution” watermarking, making the hidden data detectable even if only a small fragment of the page is captured.
B. The “Blind” Extraction Advantage
The “Blind” aspect is technically significant. In digital watermarking, there are two types of extraction:
-
Non-Blind: Requires the original, un-watermarked file to compare against the suspected leak.
-
Blind: The extraction algorithm can retrieve the hidden code without needing the original source file.
For users of VeryPDF DRM Protector, this means if a document is found on a pirate forum, you simply run the leaked file through the VeryPDF Forensic Tool. The system will “read” the invisible noise and output the exact user ID responsible for the leak, even without the master copy on hand.
3. Resilience Against the “Analog Hole”
One of the greatest threats to DRM is the Analog Hole—the point where digital content is converted into a physical or visual form (like a screen display) that can be re-recorded.
VeryPDF’s Blind Watermark is engineered to survive these common “attacks”:
-
Screen Capturing/Snipping: Because the watermark is embedded in the frequency of the image data, a screenshot retains enough of the underlying mathematical pattern for the watermark to remain detectable.
-
Print-and-Scan: If a user prints a protected PDF and then scans it back into a digital format, the core frequency components often survive the transition, allowing for forensic tracing.
-
Format Shifting: Converting a PDF to a series of JPEGs or a Word document often fails to strip the blind watermark, as the data is woven into the visual representation of the text and images.
4. Key Features in VeryPDF DRM Protector
The integration of Blind Watermarking into VeryPDF DRM Protector provides a multi-faceted security suite:
Dynamic Forensic Personalization
Every time a user opens or downloads a PDF, VeryPDF can inject a unique, invisible ID. If “User A” leaks the document, their specific ID is embedded. If “User B” leaks it, a different ID is present. This creates a powerful psychological deterrent; when users know a document is forensically “signed” to them, they are significantly less likely to share it.
No Impact on File Performance
Advanced watermarking often slows down document rendering. VeryPDF’s optimized algorithms ensure that the embedding process happens in milliseconds, and the resulting file size increase is negligible.
Seamless Integration with Existing DRM
Blind Watermarking acts as the “Second Line of Defense”.
-
Line 1: DRM Encryption (prevents unauthorized opening).
-
Line 2: Blind Watermarking (tracks the source if the user bypasses Line 1 via a camera or screenshot).
5. Strategic Benefits for Industry Leaders
Corporate & Legal
In high-stakes litigation or M&A (Mergers and Acquisitions), leaking a confidential PDF can result in millions of dollars in losses. VeryPDF allows firms to share sensitive documents with the confidence that any leak can be traced back to the specific workstation or individual responsible.
Education & E-Learning
Course creators often find their premium PDFs on “shadow libraries.” By using Blind Watermarks, publishers can identify which student account was used to scrape the data, allowing them to take legal action or revoke access.
Government & Intelligence
For classified memos, the “Invisible” nature of the watermark is vital. It allows for tracking without alerting the perpetrator that the document is tagged, facilitating internal investigations into data breaches.
6. Implementation Strategy: How to Deploy
Using VeryPDF DRM Protector to apply these watermarks is a streamlined process:
-
Input: Upload your source PDF.
-
Configuration: Select the “Blind Watermark” option. Define what data to embed (e.g.,
%UserEmail%,%IPAddress%,%DateTime%). -
Protection: The DRM engine encrypts the file and embeds the frequency-domain watermark simultaneously.
-
Distribution: Distribute the protected PDF via your web portal or email.
7. The Future of PDF Security
As AI-based image manipulation becomes more common, the need for robust, invisible forensic tools will only grow. VeryPDF is committed to evolving its algorithms, exploring Deep Learning-based watermarking which uses neural networks to hide data in ways that are even more resistant to heavy distortion.
By choosing VeryPDF DRM Protector with Blind Watermarking, you are not just buying a software tool; you are investing in a long-term security strategy that protects the integrity, value, and exclusivity of your digital content.
Conclusion
The Blind Watermark is the ultimate safeguard for PDFs in today’s digital age. Acting as an invisible, silent, and tamper-proof security layer, it creates an unbreakable link between your sensitive documents and their authorized users. With VeryPDF DRM Protector, your PDFs are not only encrypted and protected from unauthorized access, but each file also carries a unique forensic watermark that can trace any leaks back to the source. This means you no longer need to worry about how your PDF was copied or shared—you can focus entirely on who is responsible. Whether it’s for corporate reports, e-learning materials, legal contracts, or government documents, this powerful combination of digital watermarking, PDF security, and DRM technology gives you the confidence and evidence you need to prevent data breaches, stop piracy, and protect your business assets.