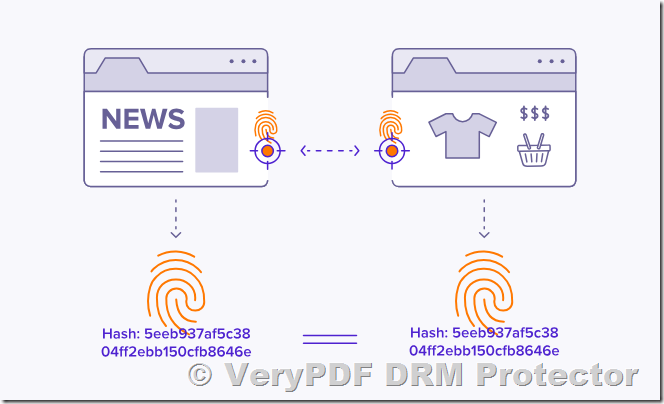
In the digital security landscape, hardware fingerprint, browser fingerprint, and device fingerprint are powerful technologies used to uniquely identify and authenticate a user’s device. These identifiers help enforce strict access control, preventing unauthorized users from opening protected files on unregistered systems. VeryPDF DRM Protector leverages these advanced fingerprinting techniques to ensure that only approved devices and browsers can access DRM-protected PDFs, significantly reducing the risk of unauthorized sharing and content leakage.
What is Hardware Fingerprint?
A hardware fingerprint is a unique identifier generated based on the physical components of a device. This can include:
- CPU ID
- Motherboard serial number
- Hard drive ID
- Network adapter MAC address
When a PDF is protected using hardware fingerprinting, it is locked to a specific machine. Even if the file is copied to another computer, it cannot be opened unless the hardware matches the registered fingerprint.
What is Browser Fingerprint?
A browser fingerprint is a set of characteristics that uniquely identify a web browser. This includes:
- Installed plugins
- Browser version and settings
- Screen resolution
- User agent information
VeryPDF DRM Protector can use browser fingerprinting to restrict access based on the specific browser being used. This prevents users from bypassing security restrictions by switching browsers or using private/incognito modes.
What is Device Fingerprint?
A device fingerprint is a broader identifier that combines hardware and browser fingerprints along with other system parameters like:
- Operating system details
- Time zone settings
- Installed software configurations
By using device fingerprinting, VeryPDF DRM Protector ensures that a PDF file can only be opened on the exact registered device, whether it is a Windows PC, Mac, iPhone, iPad, or Android device.
How VeryPDF DRM Protector Uses These Fingerprints to Secure PDFs
- Fingerprint Collection – When a user first accesses a DRM-protected PDF, VeryPDF DRM Protector collects unique hardware, browser, and device fingerprints.
- Authentication and Registration – The software registers the user’s device and stores its fingerprint in a secure system.
- Access Control – Each time the user attempts to open the file, VeryPDF DRM Protector verifies the current device fingerprint against the stored data.
- Access Denial for Unrecognized Devices – If the fingerprint does not match (e.g., the file is copied to another device or accessed from an unauthorized browser), access is denied.
By combining hardware, browser, and device fingerprinting, VeryPDF DRM Protector provides a highly secure and flexible solution for businesses, educational institutions, and publishers looking to prevent unauthorized sharing, copying, and distribution of their confidential PDFs.
Custom-Built DRM Protection: Tailored Security with Fingerprint Technology
VeryPDF DRM Protector not only offers powerful built-in DRM protection features but also provides a custom-built version that allows businesses and organizations to implement hardware, browser, and device fingerprinting according to their specific security needs. This customization ensures that PDF protection aligns with unique operational requirements, whether for corporate document control, educational content security, or confidential data protection.
What is the Custom-Built DRM Service?
The custom-built version of VeryPDF DRM Protector is a fully customizable DRM solution that extends the standard security features by allowing users to:
- Define Advanced Fingerprint Rules – Specify which hardware components, browser settings, or device identifiers should be used for authentication.
- Set Custom Access Policies – Restrict access based on company-specific security guidelines, ensuring PDFs are only accessible in designated environments.
- Integrate with Existing Systems – Seamlessly incorporate DRM protection into existing document management, learning management, or enterprise security systems.
- Enable Regional or Device-Based Restrictions – Prevent file access from unauthorized locations, networks, or devices.
How the Custom DRM Solution Works
- Requirement Analysis – VeryPDF’s development team works closely with customers to understand their specific security needs.
- Custom Implementation – Unique fingerprinting rules and access control mechanisms are integrated into the DRM system.
- Testing & Deployment – The tailored DRM protection is tested to ensure it meets security expectations before final deployment.
- Ongoing Support & Upgrades – Customers receive continuous support and updates to keep their DRM system secure and up to date.
Who Can Benefit from the Custom-Built DRM Version?
- Enterprises handling confidential reports that require strict device-based access control.
- Educational institutions protecting online learning materials from unauthorized distribution.
- Publishers and content creators securing digital publications from piracy.
- Government agencies managing sensitive documents that must remain restricted to authorized devices only.
For businesses and organizations that need tailored DRM solutions with advanced fingerprint protection, VeryPDF offers free custom development services. Contact their support team at http://support.verypdf.com/ to discuss your requirements and get a solution designed specifically for your needs.
Popular Keywords for Device-Based PDF Security Solutions,
- Lock PDF to a specific device
- Restrict PDF access to authorized devices only
- Bind PDF to a single registered device
- Prevent PDF access from unregistered devices
- Secure PDF with device-based restrictions
- Allow PDF viewing only on designated devices
- Protect PDF with hardware-based authentication
- Limit PDF access to predefined devices
- Enforce device-specific PDF security
- Ensure PDFs can only be opened on approved devices
- Implement device-level access control for PDFs
- Restrict PDF usage to company-approved devices
- Prevent unauthorized device access to PDFs
- Secure PDF files with custom device binding
- Enable strict device authentication for PDFs
- Assign PDF access permissions based on device ID
- Lock PDF files to unique device fingerprints
- Set device-specific restrictions for PDF viewing
- Ensure PDF documents remain restricted to intended users
- Use device binding to prevent unauthorized PDF sharing
- Lock PDFs to Specific Devices for Maximum Security
- Restrict PDF Access to Authorized Devices Only
- Bind PDFs to a Single Registered Device
- Prevent Unauthorized Devices from Opening PDFs
- Secure PDF Access with Hardware-Based Authentication
- Limit PDF Viewing to Predefined Devices
- Enforce Device-Specific PDF Security Controls
- Ensure PDFs Are Only Accessible on Approved Devices
- Implement Device-Level Access Control for PDFs
- Enable Custom Device Restrictions for Secure PDF Viewing