In an increasingly digital world, safeguarding documents is crucial, especially when they contain sensitive or confidential information. One powerful tool to help prevent unauthorized sharing and tampering of documents is dynamic watermarking. While traditional watermarks served as visible marks on paper, dynamic watermarks offer a far more sophisticated and flexible method of document protection in the digital realm.
This article will explore what dynamic watermarks are, why they are important, and how to effectively apply them to protect your documents.
https://drm.verypdf.com/online/
What Are Dynamic Watermarks?
Dynamic watermarking refers to the use of watermarks that change in real-time based on context, such as the recipient of the document, the time and date it was opened, or even the specific device used to view it. Unlike static watermarks, which remain the same regardless of when or by whom a document is accessed, dynamic watermarks can adapt, providing greater security and customization.
For instance, a dynamic watermark could include the recipient’s name, email address, or even the date and time the document was opened. This makes the watermark more than just a decorative element; it becomes a tool for tracking, identification, and deterrence.
Why Are Dynamic Watermarks Important?
Dynamic watermarks are not just an aesthetic feature but a critical component of document protection for several reasons:
- Traceability: They make it easy to trace the source of a document if it is leaked or shared without authorization. By embedding identifiable information such as the recipient’s name or email, dynamic watermarks provide a clear trail of accountability.
- Real-time Updates: Static watermarks are static by definition, which means they cannot be updated after the document is created. Dynamic watermarks, however, can reflect real-time information, such as the time of viewing, preventing discrepancies between when the document was distributed and when it was accessed.
- Discouraging Unauthorized Sharing: Dynamic watermarks can serve as a powerful deterrent against the unauthorized distribution of documents. For example, displaying a recipient’s name on the watermark discourages sharing the document with others since the document is personally identifiable.
- Legal Protection and Compliance: For documents containing confidential or regulated information, dynamic watermarks provide an additional layer of legal protection. They make it clear who was the intended recipient, and if the document is misused, it’s easier to establish liability.
How to Add a Dynamic Watermark to a Document
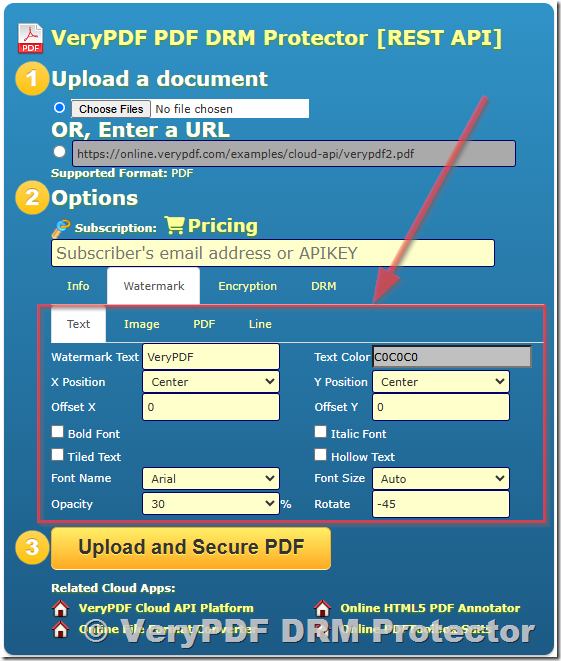
Adding a dynamic watermark to a document can be done using specific software solutions designed for digital rights management (DRM). One of the most effective tools for this is VeryPDF DRM Protector, which allows users to add dynamic watermarks to PDFs.
Here’s how to add a dynamic watermark to a document:
- Choose a Reliable DRM Solution: First, you’ll need a solution that offers robust security and watermarking features. VeryPDF DRM Protector is a top choice since it integrates well with PDF files and provides advanced security features, including dynamic watermarking.
- Set Up the Watermark: With DRM software like VeryPDF, you can create a dynamic watermark using variables that will automatically update when the document is opened. For example, you can add the recipient’s name and email, the date and time the document is opened, and other relevant information.
- Apply the Watermark to Your Document: Once you’ve set up the variables, the software will automatically insert the dynamic watermark into your document when it is viewed. This ensures that the watermark remains visible and accurate for each recipient.
- Lock Document Editing: Dynamic watermarking works best when combined with other DRM controls, such as restricting document editing and preventing unauthorized access. With DRM protection, the watermark cannot be removed or altered, ensuring that it serves as a permanent security feature.
Best Practices for Implementing Dynamic Watermarks
To make the most of dynamic watermarks, it’s essential to consider a few best practices:
- Combine with Other DRM Features: Dynamic watermarking alone isn’t enough. It should be part of a comprehensive document protection strategy that includes encryption, access control, and audit tracking. This way, even if a watermark is somehow bypassed, the document is still protected through other measures.
- Ensure Watermark Visibility: Make sure the watermark is visible enough to deter unauthorized sharing but not intrusive enough to interfere with the document’s readability. Dynamic watermarks should be strategically placed to be effective without detracting from the document’s content.
- Test Across Devices: Different devices may display watermarks differently. Ensure that your watermark solution works well across a range of devices to ensure consistency and effectiveness.
- Regularly Update Watermark Settings: For documents that are likely to be accessed or shared over time, consider updating the dynamic watermark periodically to ensure it reflects accurate and up-to-date information.
Dynamic Watermarks with VeryPDF DRM Protector
One of the most effective ways to apply dynamic watermarks is through VeryPDF DRM Protector. This software allows you to add both static and dynamic watermarks to PDF documents, with several key advantages:
- No Plugins or JavaScript: Unlike many other watermarking tools, VeryPDF DRM Protector doesn’t rely on plugins, JavaScript, or browser-based security, all of which can be bypassed or compromised.
- Prevents Document Editing: With DRM protection, documents can’t be edited, ensuring that the watermark remains intact and non-removable.
- Accurate Time and Date Stamps: VeryPDF DRM Protector can pull accurate time data from cloud servers or the device itself to ensure that the watermark reflects the correct time and date of document access.
- Prevents Unauthorized Sharing: The software also locks documents to authorized devices, ensuring that watermarks cannot be removed, and documents cannot be shared on unauthorized platforms.
FAQs
Can you add a dynamic watermark in Word?
Not natively. However, using solutions like VeryPDF Word to PDF Converter, you can convert Word documents to PDFs and then add dynamic watermarks. However, watermarks added this way can be easily removed, so a more secure solution like VeryPDF DRM Protector is recommended.
Do dynamic watermarks act as a deterrent?
Yes, they add an extra layer of security. By embedding personalized information (such as a recipient’s name and email address), dynamic watermarks discourage users from sharing sensitive documents without authorization.
Can VeryPDF DRM Protector add static text watermarks?
Yes, VeryPDF DRM Protector can add both static and dynamic text watermarks, as well as static image watermarks (e.g., logos). These watermarks can be customized with different fonts, colors, sizes, and positions.
Where does VeryPDF DRM Protector get date and time information from?
VeryPDF DRM Protector pulls accurate time data from a cloud or self-hosted server. If the document is being accessed offline, the software uses the system time, but it also checks for tampering of the system clock.
Can you add a recipient’s email to a watermark?
Yes, with VeryPDF DRM Protector, you can use variables like %Email% to automatically insert the recipient’s email address into the watermark.
Conclusion
Dynamic watermarks are a powerful tool for protecting your documents, deterring unauthorized sharing, and ensuring the security of sensitive information. By embedding personalized, time-sensitive information into the watermark, you can track and prevent the leakage of documents. When combined with DRM features like access control, encryption, and editing restrictions, dynamic watermarks provide robust protection against unauthorized access and distribution. For the most effective results, use a solution like VeryPDF DRM Protector, which integrates dynamic watermarking with a comprehensive set of DRM controls to safeguard your documents.